Conti Targets VMware – 3 Things to do NOW
• January 10, 2022

Russian cybercrime syndicate Conti has singled out VMWare vCenter and Horizon from the millions of systems vulnerable to Log4j. vCenter and Horizon, the brains of your virtual environment, are being actively exploited to transmit ransomware and seek out vulnerable systems BEHIND your firewall. Once the bad guys gain access, almost every vendor or component has a vulnerability and can be exploited. This has given rise to the most advanced attack to date by the largest advanced ransomware group, Conti. This group is the first professional crimeware outfit to adopt and weaponize the Log4Shell vulnerability.
They’ve built up a holistic attack chain; a recipe to get inside your network and stop your business dead. How long could your business last without its data? How long until you’d have to pay the ransom?
This is a zero-day attack which means there are no patches or updates and decreasing your vulnerability requires manual fixes or workarounds.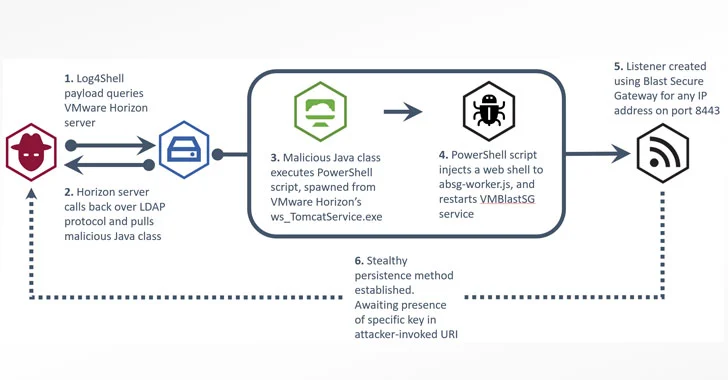
If you are running vCenter (or any of the other products affected by the Log4j vulnerability), here are a few things you can do to stay off Conti’s radar:
· Buy Time – Because so many systems are vulnerable, you’ll need time to figure out what you need to fix. Some organizations will need months to identify and fix their vulnerabilities, so it’s time to circle the wagons. Constantly monitor inbound traffic and lateral traffic inside the network and shut down any suspicious activity. Limit access by enforcing your MFA/Identity protections.
· Identify the affected machines – Create a repeatable process to discover and mitigate vulnerabilities. Cybercriminals are extremely innovative; once you plug these holes, they’ll find a way to exploit something else, so you need a consistent process to quickly identify a breech.
· Plan for the worst – Have a comprehensive business recovery plan that has you back in business within hours, not months. The plan should position your organization to recover ALL your data. Only 8% of companies get all their data back, even when they pay the ransom. Make sure your plan gets your entire data center and all applications up and running; if you only get the data, what are you going to do with it? And finally, it is critical to ensure your plan includes all your desktops and remote users. If your employees can’t work, that’s not recovery.
Many of our clients are working through this situation with our assistance. Mavenspire’s SMARTaaS Recovery service lets you ignore the ransomware demands and get your business back to work within hours. If you’d like to learn more and get a free estimate, click here.